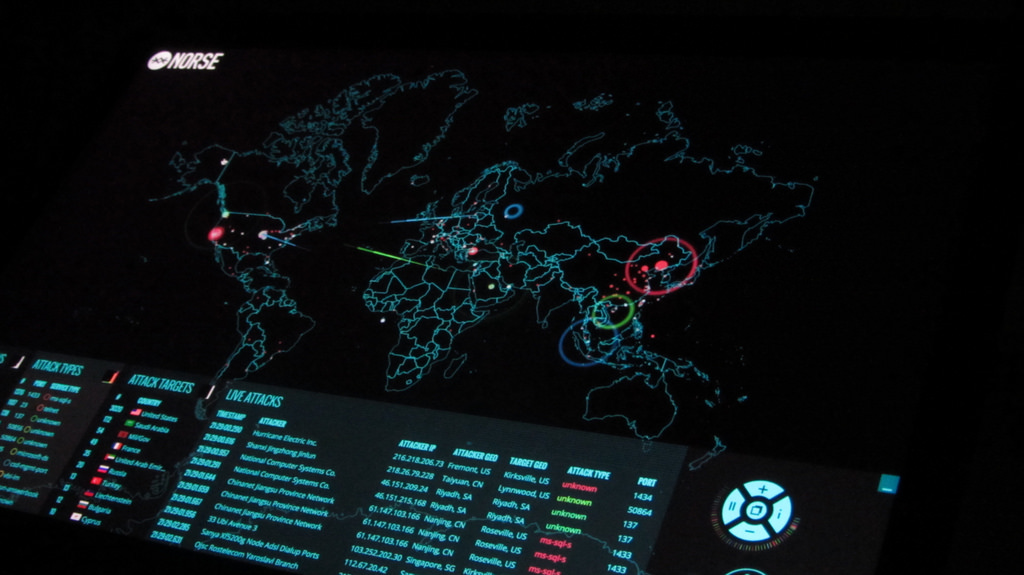
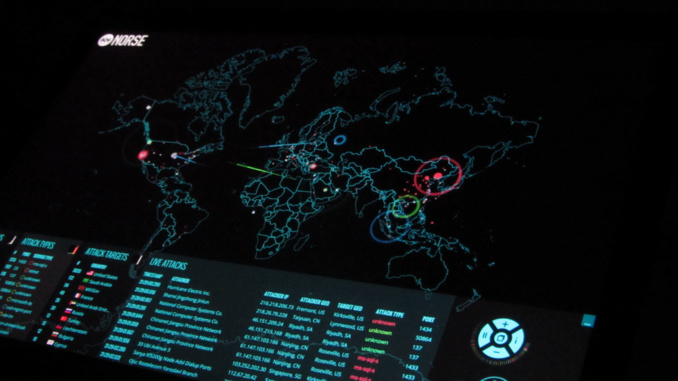
Yesterday, the ECB announced commencement of the first pan-European program, during which participants in the financial market will be tested for strength against cyber attacks. The project is called the "European Framework for Threat Intelligence-based Ethical Red Teaming - TIBER-EU". The program is advisory in nature as the ECB notes that EU member states can decide for themselves when and how to conduct similar inspections of their financial institutions. At the same time, the ECB stresses that no "satisfactory" or "unsatisfactory" assessments will be issued following the inspections’ results. They will only give recommendations on improving the specific security system of a financial institution.
The ECB notes that cyber defense will be checked for strength by both regular staff and independent cyber security specialists. At the same time, comments to the TIBER-EU program state that "the authorities will admit the test is passed only if they are attended not only by internal specialists, but also by external parties." The ECB believes that "an external examiner gives a fresh and independent view of the solution of a problem that internal teams may not see... In addition, external testers give more resources and experience in testing the system for strength, which only serves the institution being tested."
The program’s timing will be determined separately, depending on each particular financial institution, but judging by experience, "a period of 10-12 weeks is a reasonable period for such a check." In the course of tests it is proposed to employ "a full range of techniques that real hackers use." In particular, the ECB suggests subjecting critical systems of financial institutions, including key units, to cyber attacks, trying to "crack" them or "interfere" with their work. As a result, reports will be prepared both by the "attackers" and by those who was subjected to the cyberattacks.
Western companies have a wide experience of asking so-called ethical computer hackers to look for errors and vulnerabilities in software products and computer networks. In the United States, similar checks have the common name of Bug Bounty. Among those who invited hackers to test systems were such corporations as Microsoft, Facebook, AT&T, Bosch, Cisco and others. A similar program is implemented by Tesla, with rewards ranging from $ 100 to $ 10 thousand. During its implementation, 285 vulnerabilities were identified, and the average reward was $ 650.
Recently, public institutions have shown interest in such inspections. In April 2016, the digital protection department of the US Department of Defense's launched the monthly "Hack the Pentagon" program. The organizers invited computer systems and networks security experts to participate in it. The hackers were looking for vulnerabilities on the external websites of the ministry, as well as were searching for solutions to eliminate these vulnerabilities. Within the framework of the program, 1,400 participants found 138 unprotected sites. 58 participants received remuneration for a total of $ 71,200. The largest prize of $ 15,000 was paid to one of the hackers who identified several vulnerabilities at once.
source: ecb.europa.eu
The ECB notes that cyber defense will be checked for strength by both regular staff and independent cyber security specialists. At the same time, comments to the TIBER-EU program state that "the authorities will admit the test is passed only if they are attended not only by internal specialists, but also by external parties." The ECB believes that "an external examiner gives a fresh and independent view of the solution of a problem that internal teams may not see... In addition, external testers give more resources and experience in testing the system for strength, which only serves the institution being tested."
The program’s timing will be determined separately, depending on each particular financial institution, but judging by experience, "a period of 10-12 weeks is a reasonable period for such a check." In the course of tests it is proposed to employ "a full range of techniques that real hackers use." In particular, the ECB suggests subjecting critical systems of financial institutions, including key units, to cyber attacks, trying to "crack" them or "interfere" with their work. As a result, reports will be prepared both by the "attackers" and by those who was subjected to the cyberattacks.
Western companies have a wide experience of asking so-called ethical computer hackers to look for errors and vulnerabilities in software products and computer networks. In the United States, similar checks have the common name of Bug Bounty. Among those who invited hackers to test systems were such corporations as Microsoft, Facebook, AT&T, Bosch, Cisco and others. A similar program is implemented by Tesla, with rewards ranging from $ 100 to $ 10 thousand. During its implementation, 285 vulnerabilities were identified, and the average reward was $ 650.
Recently, public institutions have shown interest in such inspections. In April 2016, the digital protection department of the US Department of Defense's launched the monthly "Hack the Pentagon" program. The organizers invited computer systems and networks security experts to participate in it. The hackers were looking for vulnerabilities on the external websites of the ministry, as well as were searching for solutions to eliminate these vulnerabilities. Within the framework of the program, 1,400 participants found 138 unprotected sites. 58 participants received remuneration for a total of $ 71,200. The largest prize of $ 15,000 was paid to one of the hackers who identified several vulnerabilities at once.
source: ecb.europa.eu